While I am slowly updating my blog posts with some of the topics and experiences I have with customers, I read an email discussion early this morning about landing zones between some fellow MVPs and PG members at Microsoft. The major problem I see from my experience is that there is not a good design and architecture for implementing solutions in the cloud, and that is not a technology or platform issue… I remember drawing numbers and diagrams literally with a pencil back in the days, doing the math for networks, subnetworks, DMZ, firewalls, gateways, all servers, apps and services, etc. Well… If using old school methods is not a thing anymore, I think most people still need this important foundational level. But before getting there, when I talk to partners or customers, (not generalizing), many of them don’t really know the concept of a Landing zone and why they should design and have them. Then they see the diagrams from MS Learn and suddenly they are, well, we do that… kind of! So, let’s start over.
What is an Azure Landing Zone?
An Azure Landing Zone is essentially the foundational blueprint for your cloud environment on Azure. It provides a pre-configured, scalable, and secure environment that aligns with best practices for governance, networking, identity, security, and management. Think of it as building the base structure of a house before you decide on the furniture and interior design—without a solid foundation, nothing holds up well. Right?
+---------------------------------+
| Azure Landing |
| Zone |
+------------+--------------------+
|
+------------+------------+
| Governance |
| (Management Groups, |
| Policies) |
+------------+------------+
|
+------------+------------+
| Identity & Access |
| (AAD, RBAC) |
+------------+------------+
|
+------------+------------+
| Networking |
| (VNets, NSGs, Routing) |
+------------+------------+
|
+------------+------------+
| Resource Organization |
| (Resource Groups, Tags)|
+------------+------------+
|
+------------+------------+
| Automation & |
| Monitoring |
| (IaC, Azure Monitor) |
+-------------------------+The Azure Landing Zones are a core element of Microsoft’s Cloud Adoption Framework (CAF), another topic that I often help teach within our community and clients. The CAF outlines a structured approach to cloud adoption, and landing zones complement and provide much of the underlying architecture that supports this process. They help bridge the gap between planning and operational success by ensuring that every component of your cloud environment meets operational, security, and compliance needs from day.
Deploying a Cloud Strategy starts with you. The cloud adoption works better when the first adopter has reached the level of knowledge and expertise in-house, this is known as Customer Zero, I bet you have heard this for not only Azure, but also, Power Platform, Copilot, and other Microsoft products. Once you have a clearer understanding of why ALZ matters, it will help your organization to accelerate in your adoption journey, enabling you to rapidly deploy and scale your Azure environments based on proven design patterns. By using a landing zone, you ensure consistency and compliance, that every deployed service or resource adheres to a governed set of policies, reducing risks and maintaining best practices. Last but not least, whether it’s a small project or a large enterprise deployment, landing zones are designed to grow with your needs while remaining secure and manageable, the cloud will always give you the scalability and flexibility on demand.
Some of the common issues when you are implementing an ALZ are as a result of lack of design or misconfigured settings that end up affecting management groups, subscriptions and policies that may not be enforced as expected in terms of governance. When using ARM templates or Bicep scripts, even a small syntax error or misconfigured scope (resource group versus subscription) can lead to failures. Landing zones often set up foundational networking components. Misconfigurations in Virtual Networks (VNets), subnets, or network security groups (NSGs) might impact connectivity and the overall deployment process in general, which is also very critical.
When using automation tools (like Terraform, Azure DevOps pipelines, or GitHub Actions), dependency ordering or environment variables might not be set correctly, causing intermittent issues. Ensure that your state is maintained correctly when using infrastructure as code. A mismanaged state could lead to duplicated or misconfigured resources. When using ARM templates or Bicep scripts, even a small syntax error or misconfigured scope (resource group versus subscription) can lead to failures that might take extra time to fix.
If you are using an account or service principal executing the deployment, it must have the appropriate permissions for every layer in your landing zone. Missing roles or misconfigured assignments can cause blockages by insufficient permissions, BUT… remember always to keep the least and minimum permissions as your always best practice. Service principals are very useful overall for different scenarios! More about RBAC here!
Here are some resources to study about CAF and Landing Zones, start here and make sure your team goes through this before implementing and getting into a blueprint like the one shown below. Make sure your team does all the W questions, such as what is gonna be deployed, where, why, who will be involved, and together can architect better your next project. This framework help us as a partner to do not have to reinvent the wheel, instead, we can align better all the Microsoft best practices for the cloud and our strategies to help create better solutions, maximize the usage of the cloud, manage all the cost and investments in general and having more profitability as one of your outcomes.
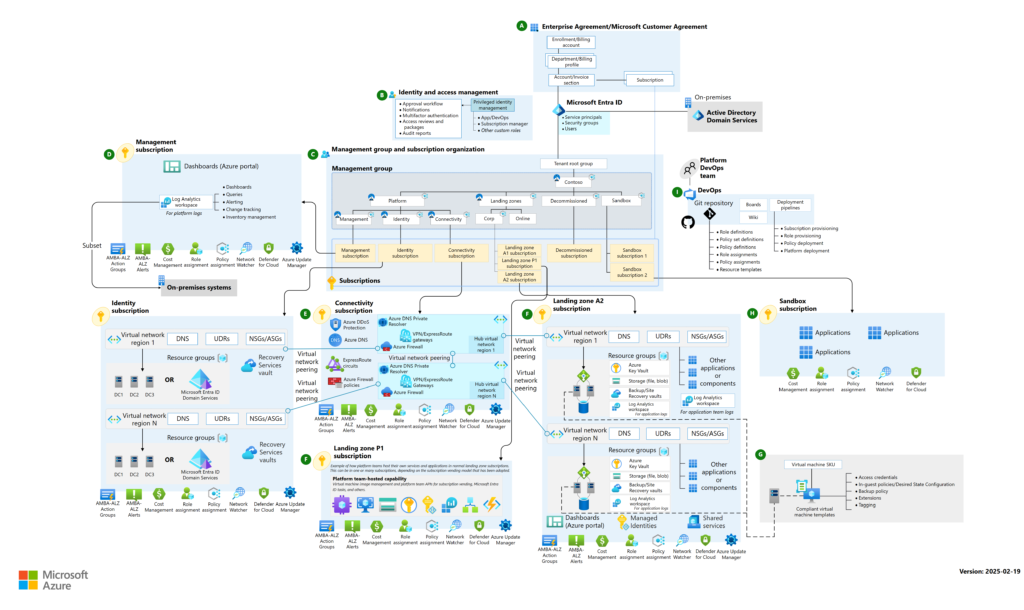
Don’t get crazy, start small…

